Bitlocker Policy Via Intune
I’ve created many policies for BitLocker in the past years, but since mid-2023, I have not played with it at all. In Dec 2023, I had a client want to create a policy in Intune, and I thought, yup, let us do it within 5 minutes. I was wrong. Microsoft has changed and issued a new Doc. since Nov 2023, and now there are many new ones.
Same Requirements:
- Intune License.
- Entra or Hybrid joined device.
- Windows 10/11.
- The device must have a TPM or Chip v. 1.2 or later (most new devices have 2.0).
- BIOS set to native EUFI.
Same roles to manage BitLocker:-
- Global Admin.
- Intune Admin
- Helpdesk Operator.
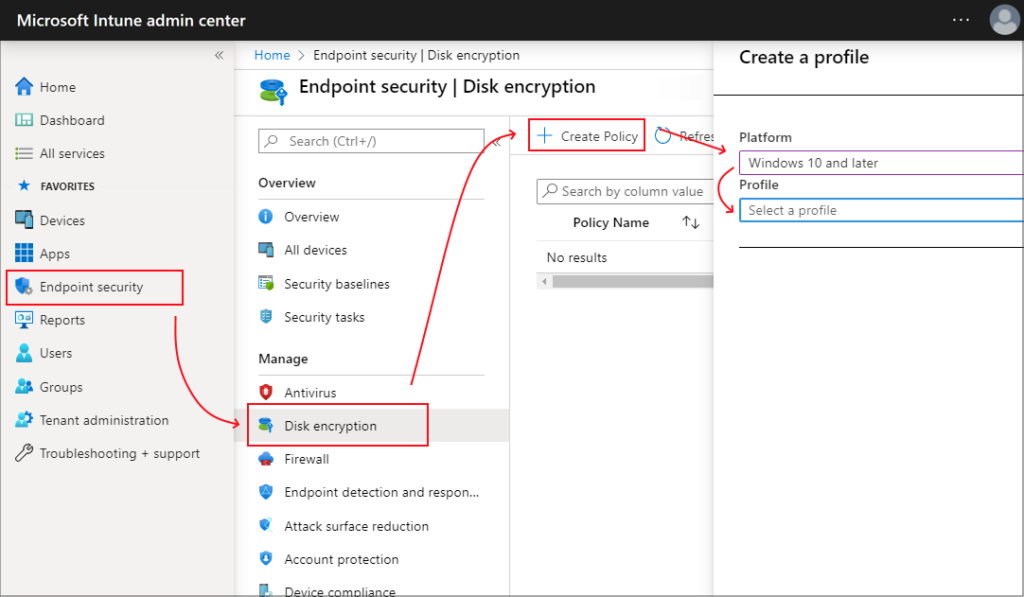
Configure the New Policy:-
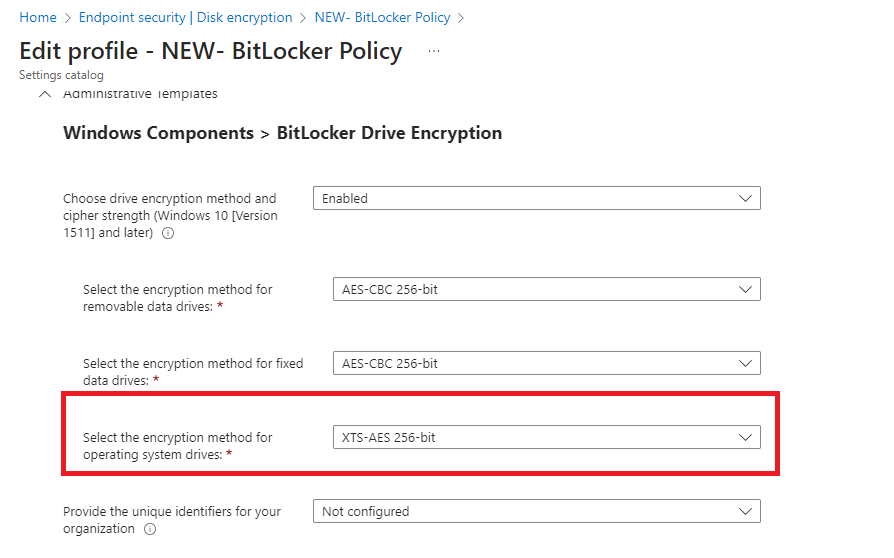
Sign in to Intine Admin Center, then Endpoint Security> DiskEncryption> click on “+” to Create Policy, as shown in the screenshot (from Microsoft).
Silent enable BitLocker
I am not going to talk about Basics because it is the same.
- Configuration Settings:
This has two settings now: BitLocker and Administrative Templets.
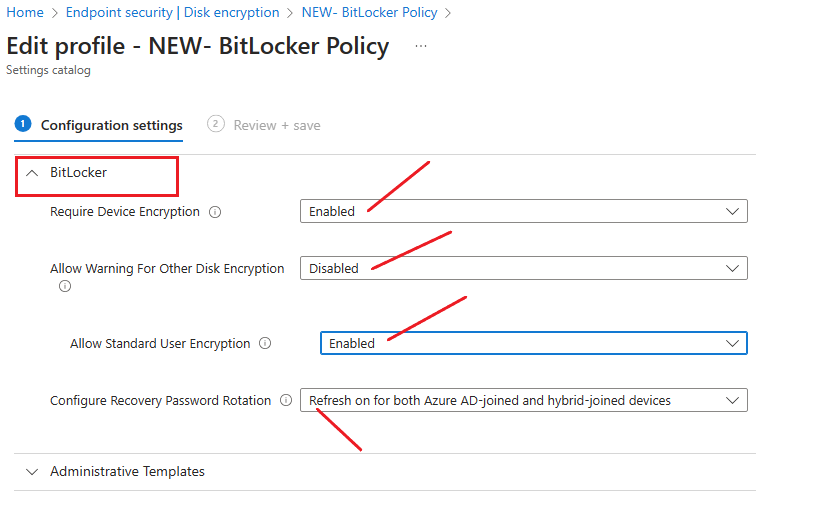
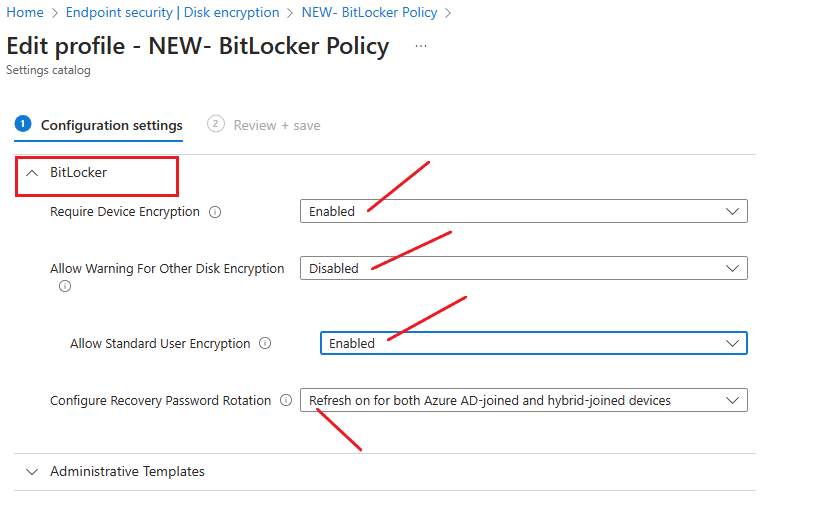
BitLocker:
Require Device Encryption: This policy is set not to configure, if you Disable it, this won’t turn off the encryption on the device but will stop the prompting to the user to turn it on. I will enable it.
Allow Warning for Other Disk Encryption: This policy is set to value =1 (the format is an integer), so the user will see the warning prompt by default, if you Disable it (values =0), the warning prompt notification won’t show up.
Allow Standard User Encryption: This policy for Other Disk Encryption, by default, this policy is set to not configure value =0, which means if the current logged in user is a non-admin policy will not try to enable encryption on any drive, if you enable it the value =1, the policy will try to enable encryption on all fixed drives even if a current logged in user is a standard user. I will Enable it.
Administrative Templets
Here we have four parts:
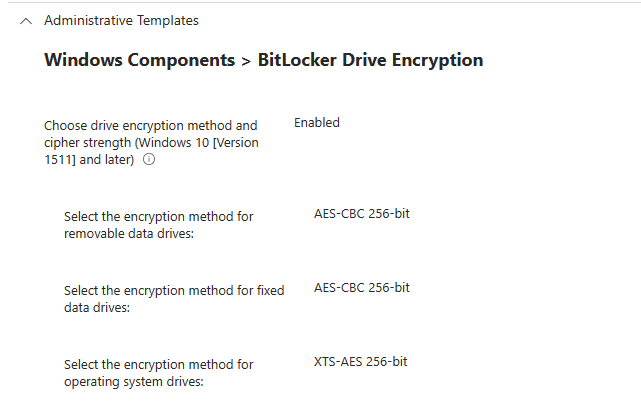
BitLocker Drive Encryption: If you Enable this policy setting you will be able to configure an encryption algorithm and key cipher strength for fixed data drives, operating system drives, and removable data drives individually.
If you Disable or do Not configure this policy setting, BitLocker will use AES with the same bit strength (128-bit or 256-bit).
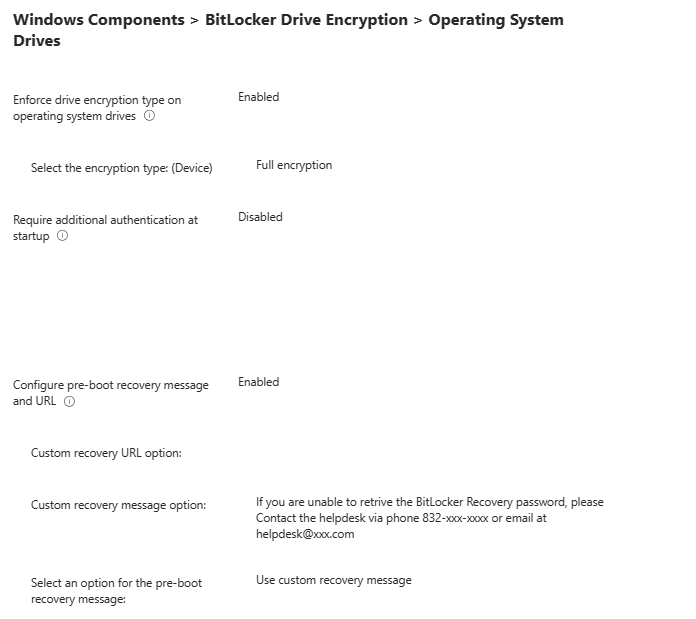
Operating System Drives: This policy allows you to configure the type of encryption; if you Disabled or Not Configure it, will allow the end user to pick the type of encryption.
If you Enable it, this will allow you to select the type of encryption among, Allow the user to choose Full encryption, Using Space Only.
Require additional authentication at startup: if you Disable or Not configure it, it won’t require additional authentication like PIN, password, etc. If enabled, it will require the user to enter a PIN, Password, etc., on startup.
Configure pre-boot recovery message and URL: This policy will allow you to give the end users some details to reach out to the helpdesk if the user has an issue with BitLocker or wants the Recovery Key.
In my case, I selected a custom message.

Fix Data Drives
Enforce drive encryption type on fixed data drives: This policy is similar to the OS policy, If you enable this policy setting the encryption type that BitLocker will use to encrypt drives is defined by this policy and the encryption type option will not be presented in the BitLocker setup wizard. If you disable or do not configure this policy setting, the BitLocker setup wizard will ask the user to select the encryption type before turning on BitLocker.
I Enabled it and selected Full Encryption
Choose how BitLocker-protected fixed drives can be recovered: This option is to select where you want the recover key to be stored. If you Enable this policy, it will let you control the methods available to users to recover data from BitLocker-protected fixed data drives. Also, you can control where to back up in AD DS (in my case, I used it, but this backed it up to Entra not AD DS) and what to back up Password and Key Packages or one of them. If Disabled or Not Configured, the default recovery options are supported for BitLocker recovery. By default a DRA is allowed, the recovery options can be specified by the user including the recovery password and recovery key, and recovery information is not backed up to AD DS.
Do not Enable BitLocker until recovery information is stored to AS DS for fixed data drives, Select True.
Allow 256-bit recovery key
Allow data recovery agent True.
Configure user storage of BitLocker recovery information, I selected “Allow 48-digit recovery password”.
Save BitLocker recovery information to AD DS for fixed data drives True.
Omit recovery options from the BitLocker setup wizard True.
Removable Data Drive
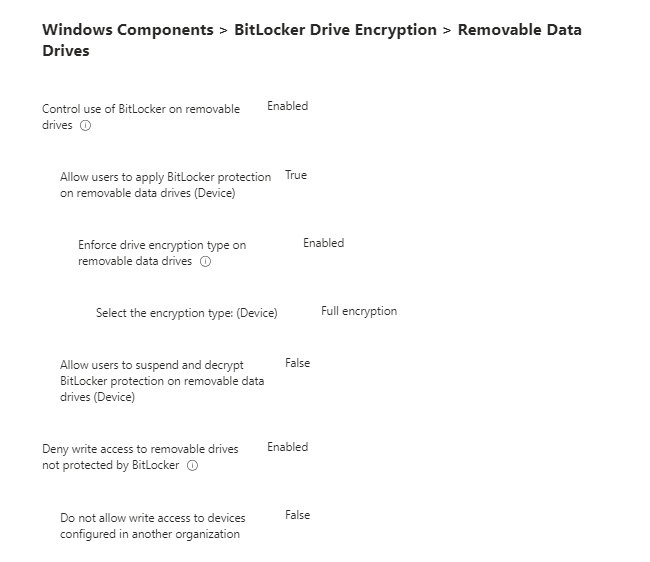
I used almost the same options as Fix Data Drives.
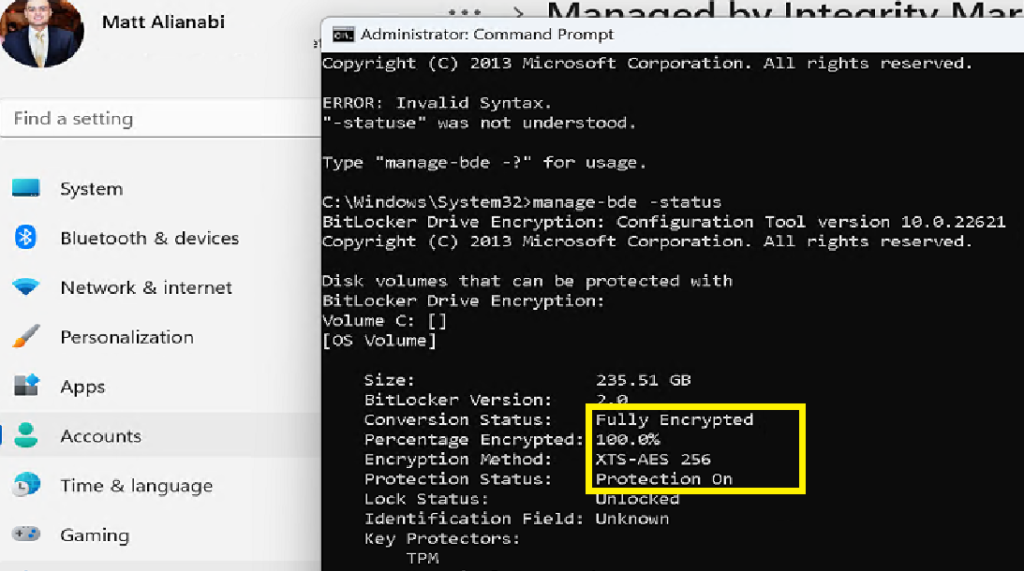
Then I deployed the policy to my test group. and logged in to one of the test devices to check the policy.
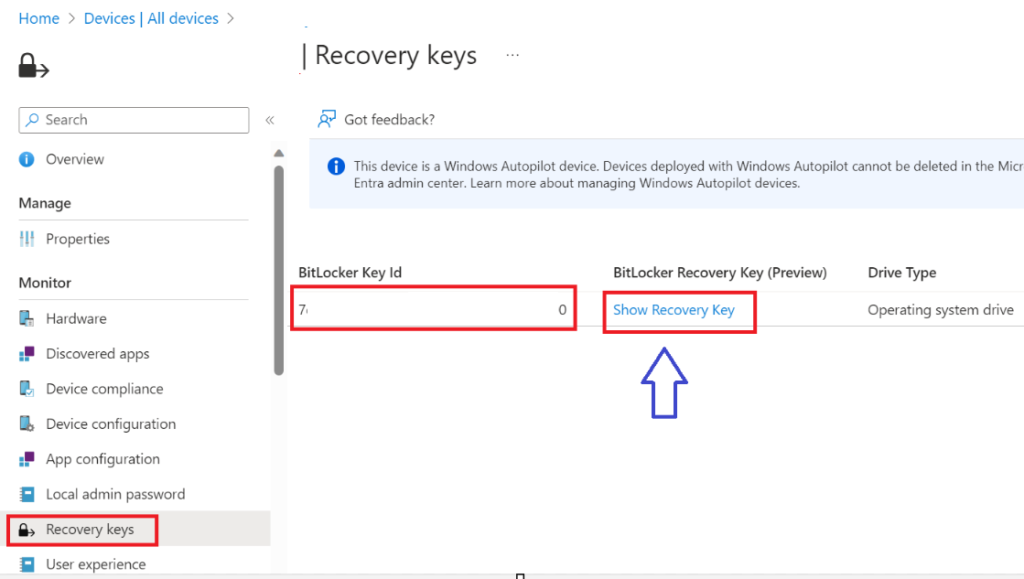
Thanks for reading. Have a nice day.