Happy New Year, everyone!
I was reading some Microsoft Articles about how to secure the Microsoft Edge Browser, and I wanted to test it. It was fun 😊.
Many companies prefer to use Edge as their default browser, which is both fast and efficient. However, we want to ensure that end users are safe and secure while using it.
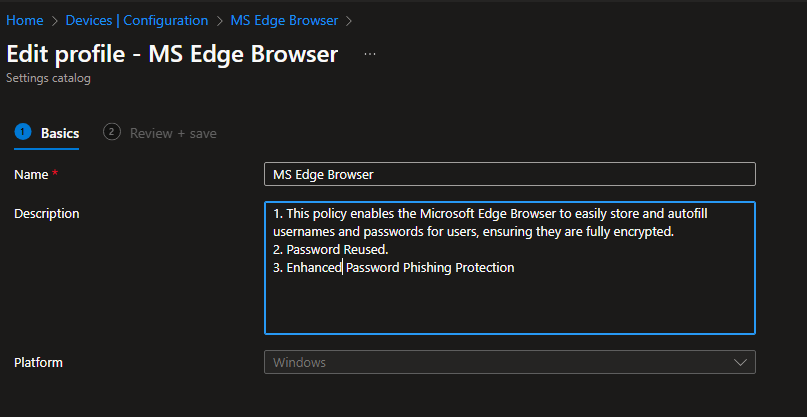
I came across a couple of Intune settings for Edge to enhance security. There are many options, but in this demo, I chose three.
1. Enable Microsoft Edge Password Manager
2. Password Reused.
3. Enhance Password Phishing Protection.
Let us take them one by one
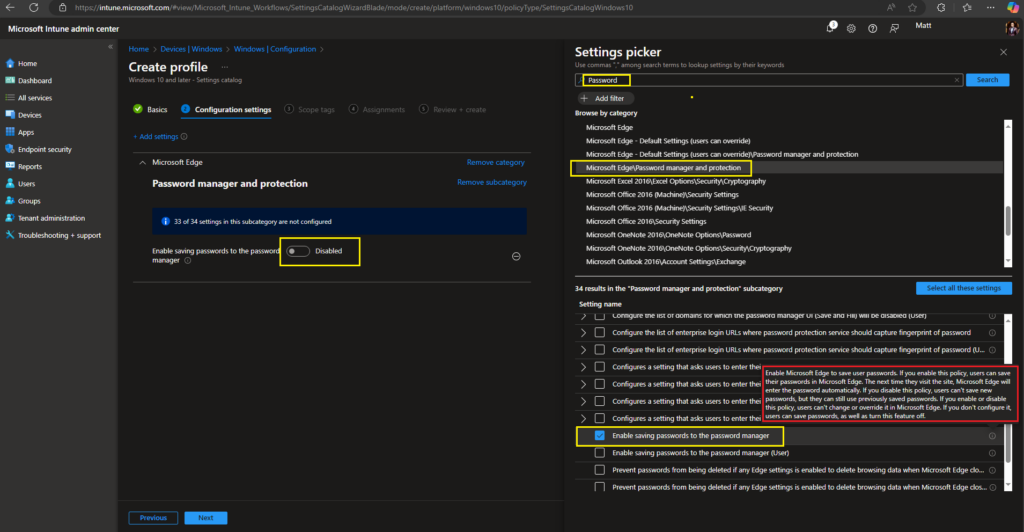
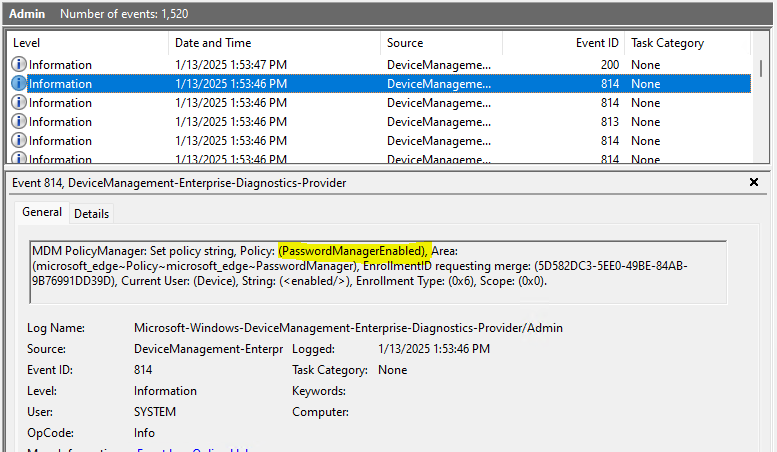
Enable Microsoft Edge Password Manager: Allow users to save their passwords in Microsoft Edge. When this policy is enabled, Microsoft Edge will automatically fill in the password the next time a user visits the site.
If you disable this policy, users can’t save new passwords, but they can still use previously saved passwords. If you enable or disable this policy, users can’t change or override it in Microsoft Edge. If you don’t configure it, users can save passwords, as well as turn this feature off.
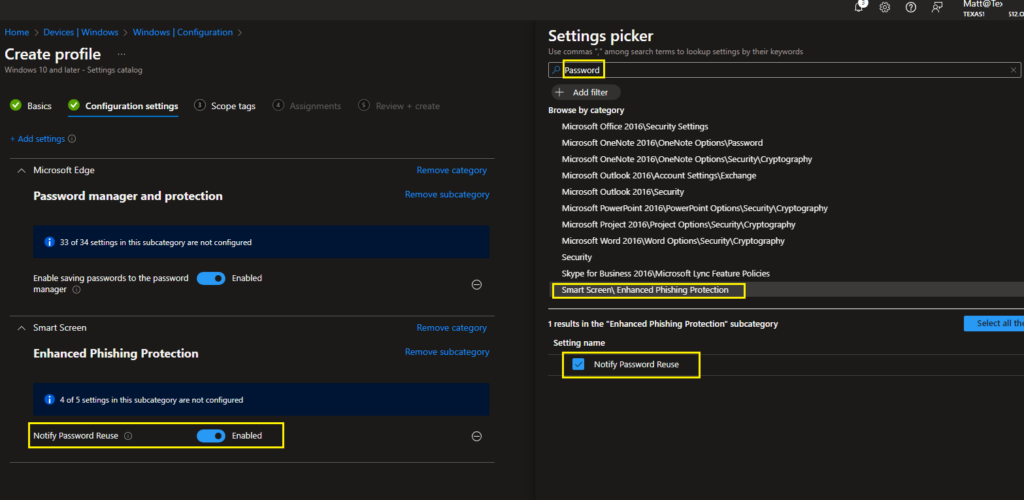
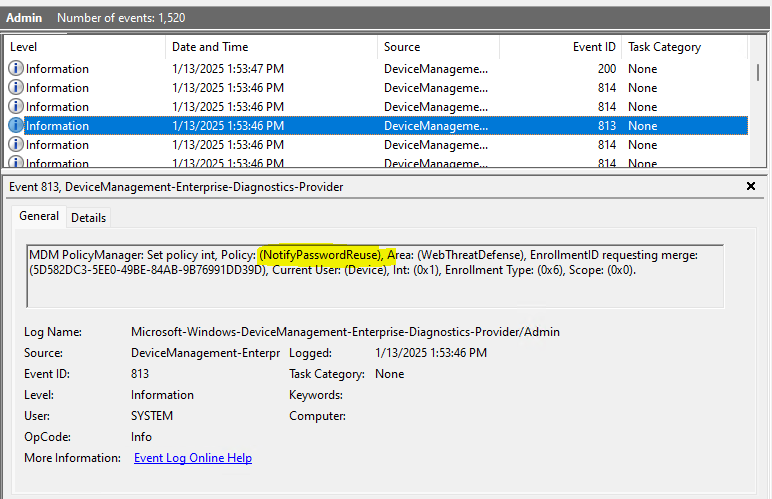
Password Reused: Configures notifications for Enhanced Phishing Protection to safeguard against password reuse.
Enhance Password Phishing Protection:
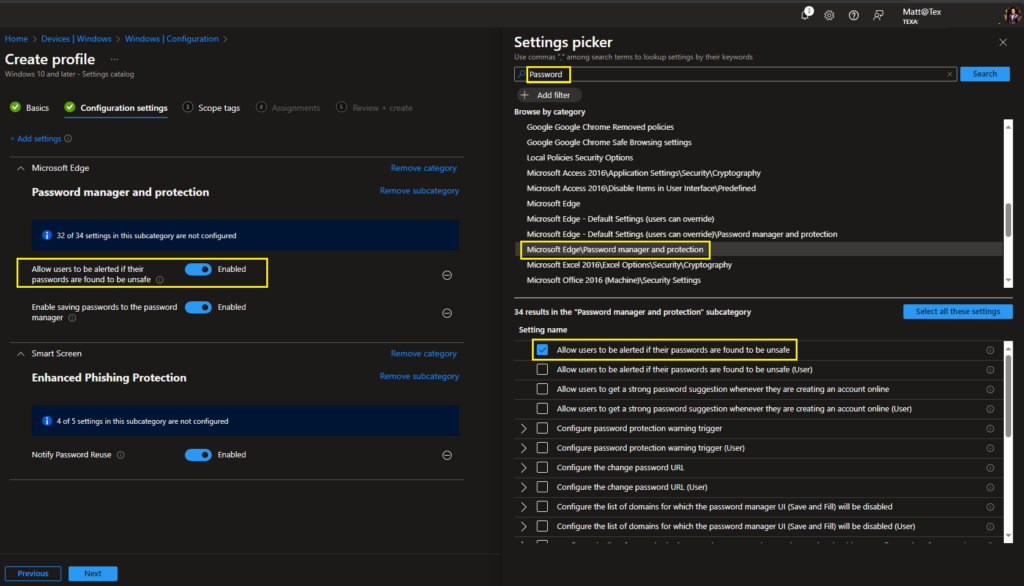
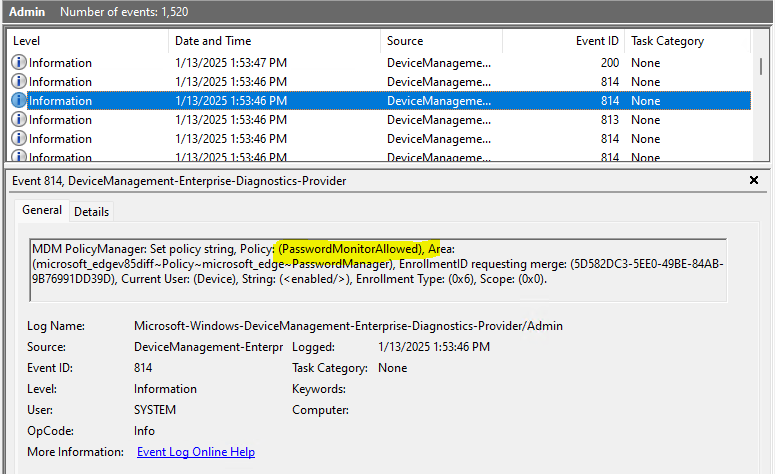
Allow Microsoft Edge to monitor user passwords. If enabled and the user consents, they will be alerted if any stored passwords are unsafe, and details will be found in Settings > Passwords > Password Monitor. Disabling this policy prevents users from receiving alerts or scanning their passwords. If enabled or not configured, users can toggle this feature.
Let us configure these settings in Intune
In Microsoft Intune Go to
Devices > Manage Devices > Configuration > Policies > Create > New Policy> Select Windows 10 and Later and Settings Catalog, then Create
For testing purposes, I assigned this Configuration to a test group which has one device
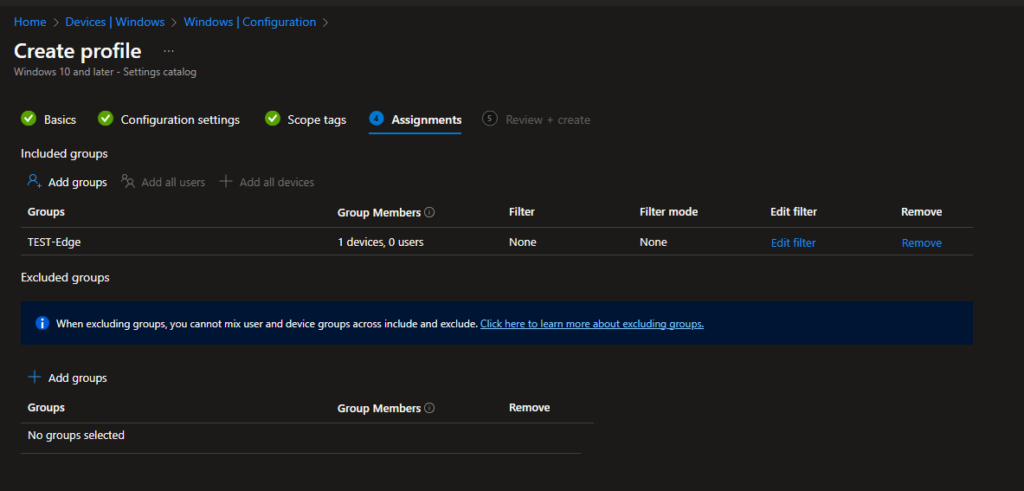
After waiting for the device to receive all the new settings, I checked the device and tried to create 3 different accounts for this demo with a weak and reused password.
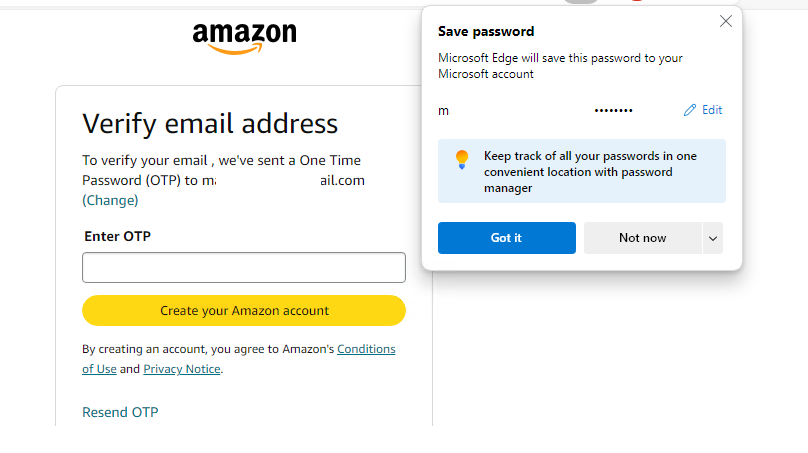
In the screenshot above, you can easily see that the browser has prompted you to save the password.
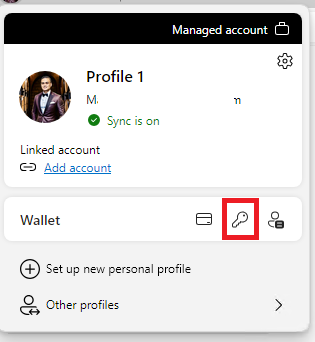
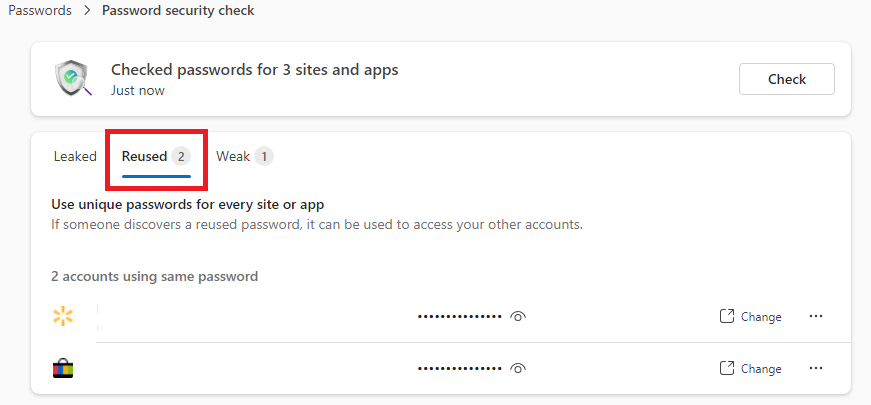
under your browser picture profile, you can see the Edge Wallet when you have saved all your Passwords, or you can use this link edge://wallet/passwords
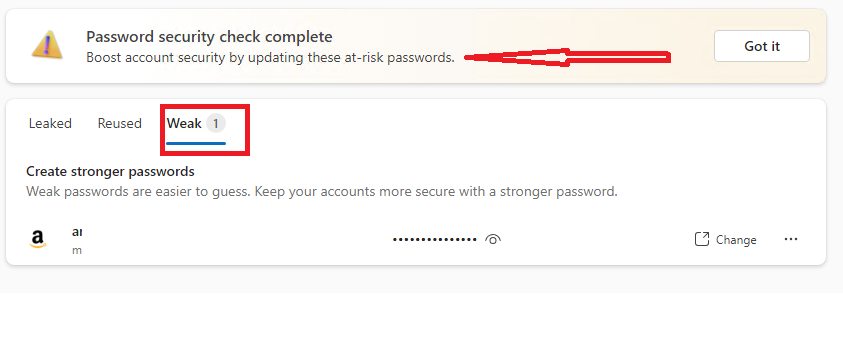
Under Password, you can see 3 different tabs: Weak, Reused, and Leaked Passwords.
You can check the event viewer to see if the policy applied or not
This is can be checked under Applications and Services Logs> Microsoft> Windows> DeviceManagement-Enterprise-Diagnostic-Provider>Admin
In this Demo I can see all policies have applied to the test device.
Thank you for reading, and have a good evening!

