In February, I was working on a request of my client to control personal devices “Windows” when the End-User tried to log in from their personal device (for any reason).
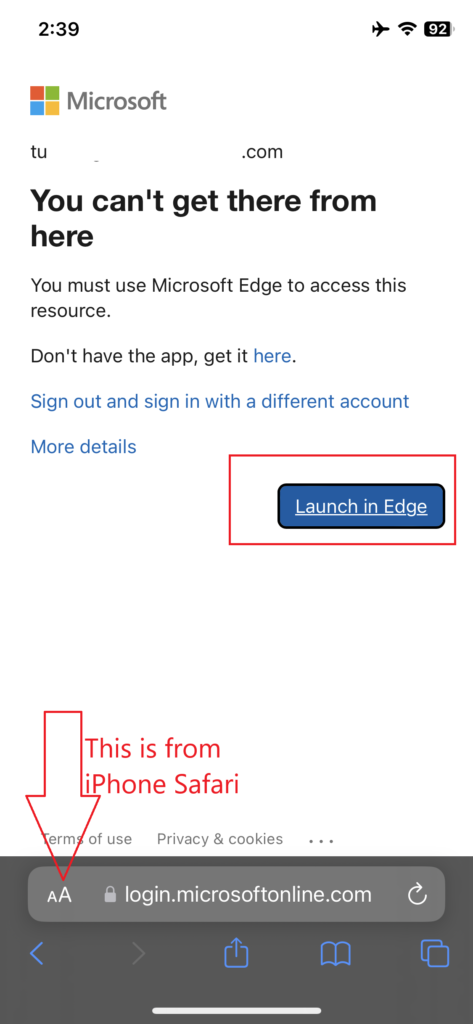
I wrote a blog about how to control that by forcing the user to use Microsoft Edge browser, and then we were able to control it. You can see the blog here.
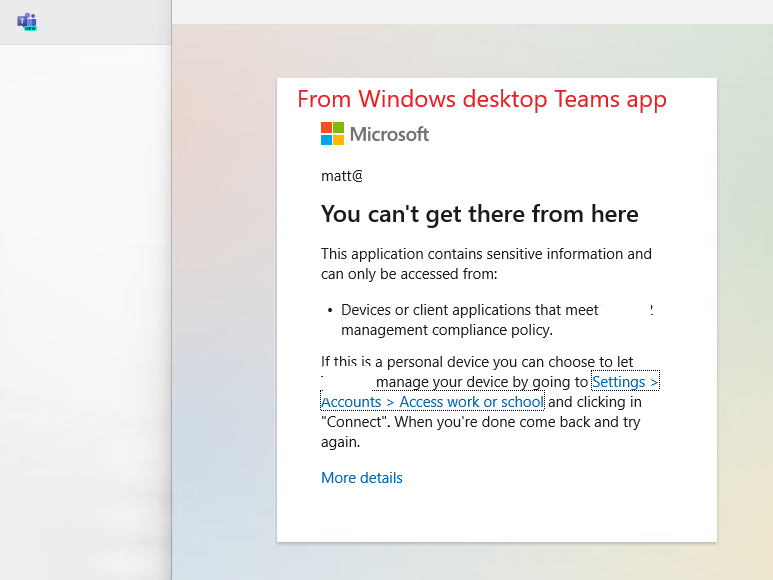
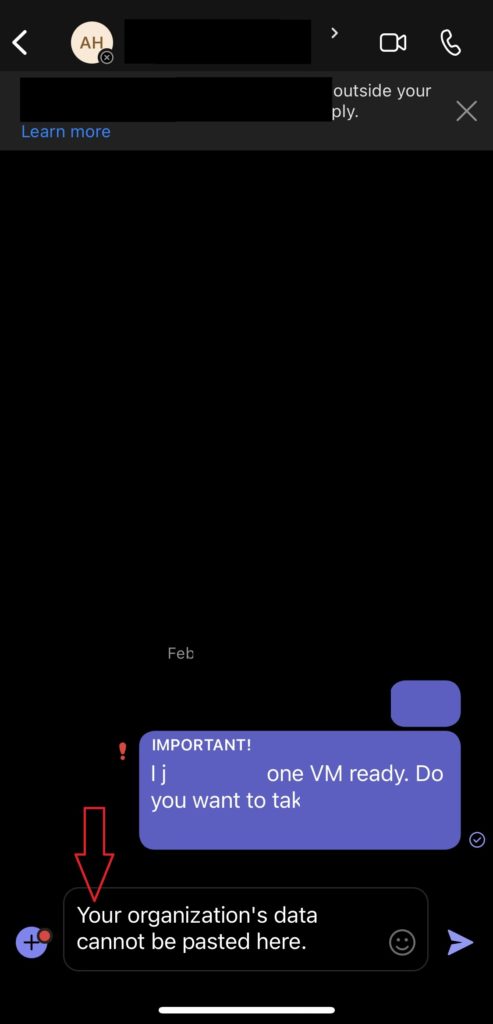
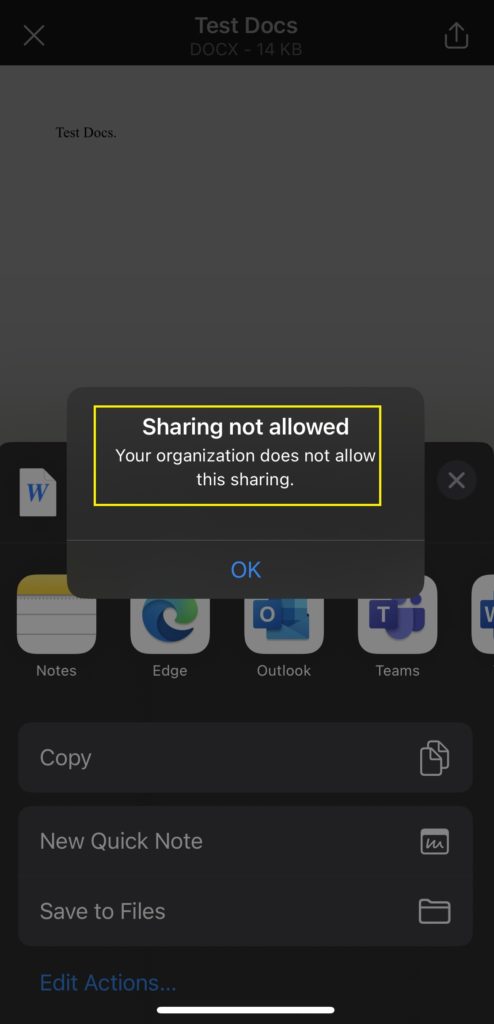
But the Cyber Security team came up with a very good question: “What if the user uses the MS Teams desktop app on their personal device?” or “What if the user uses the Teams app from their mobile device, such as an iPhone, iPad, Android, etc.” That was a good question. Everyone, including myself, has the Microsoft Teams App on their Computer and phone as well, and I know many people do these days for more convince, here I started to think about how to make the condition control that.
- Conditional Access for iOS, Android, and macOS.
- Create a Filter for devices.
- Android and iOS Apps Protection.
- Configure Access Control via SharePoint
- Conditional Access for iOS, Android, and macOS:-
Configure a new CA from Intune Admin Center > Devices> Conditional Access> New policy
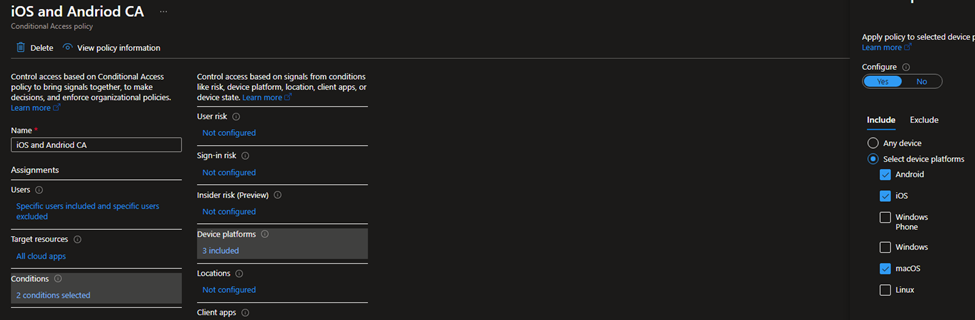
Name: give it a name.
Assignment: ensure to target a user(s) or a group of user(s), again, do not forget to Exclude your Admin account.
Target resources: in this test I target All Cloud Apps.
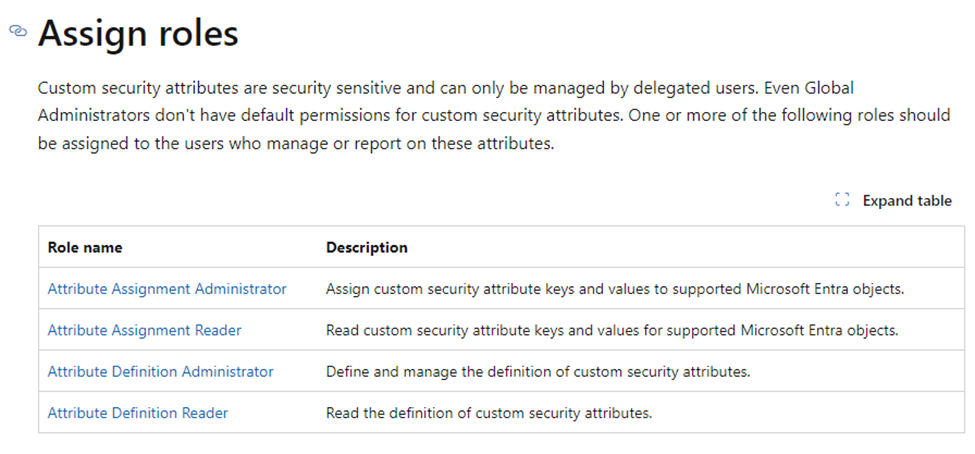
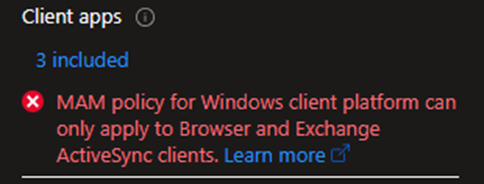
Conditions: here, we have 8 options; I selected only Device platforms (Android, iOS, macOS). Remember here that you cannot select Windows because you will get an error saying MAM works only with the browser. Also, I added a Filter here to target “Personal” devices. Note: to add a filter in CA for the first time you may see this message “You do not have the permissions needed to use custom security attributes” Yes even if you have Global Admin you cannot create, you need one of these permissions are showing below in Microsoft Doc.
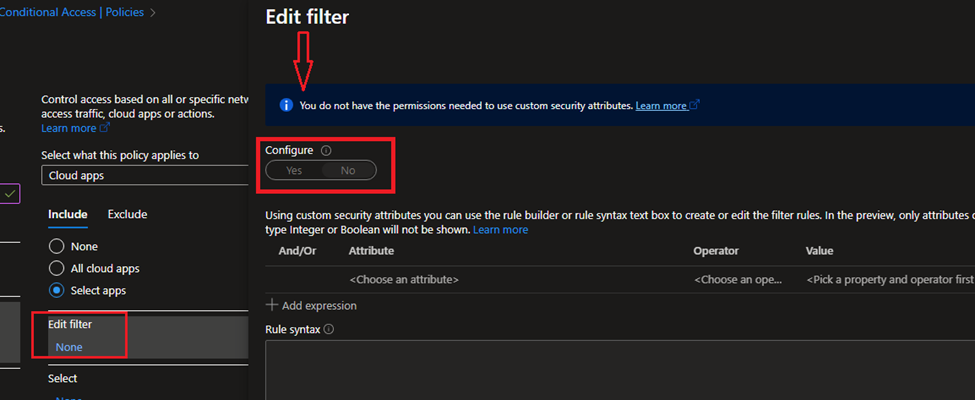
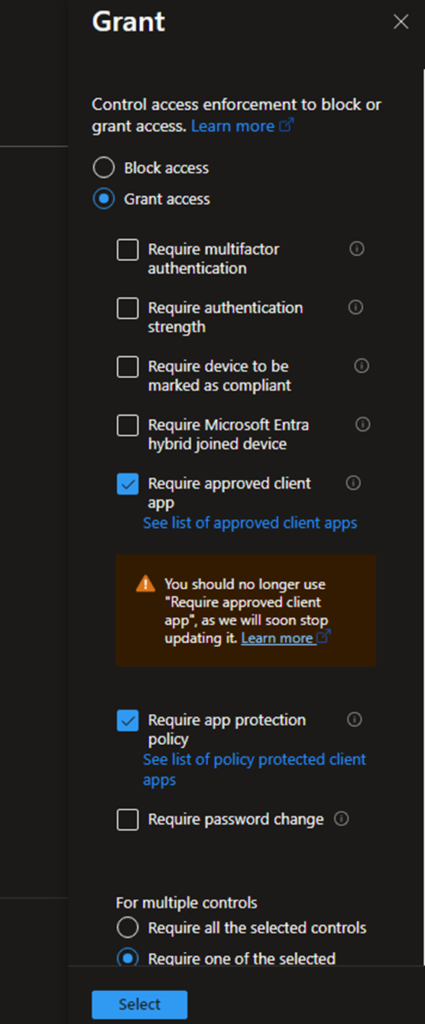
Access controls: I selected “Require Approved client app” This option will soon stop updating it, and “Require app protection policy” this option is the important one, by the way you need to select from multiple controls “Require one of the selected controls” just in case one out of support the other one will stay active.
2. Create a Filter for devices:
Devices> Filters > Create> Manage Apps
Name: Give the filter name
Platform: Select iOS or Android. Ensure to create a filter for each platform.
Rule: I want to target device management from Property Select “deviceManagementType(Device Management Type), Operator “Equals”, Value “Unmanaged”. The syntax looks like this (app.deviceManagementType—eq "Unmanaged"). You can also test the syntax by clicking on “Preview” to see if this will apply to any Apps on an unmanaged device. Next, and save.
Remember to create another one for Android if you are using it.

3. Android and iOS Apps Protection:
Apps> App protection policies> Create policy make sure to pick the right platform “Windows, iOS/iPadOS, Android”
Name: Give it a name and Description if you want.
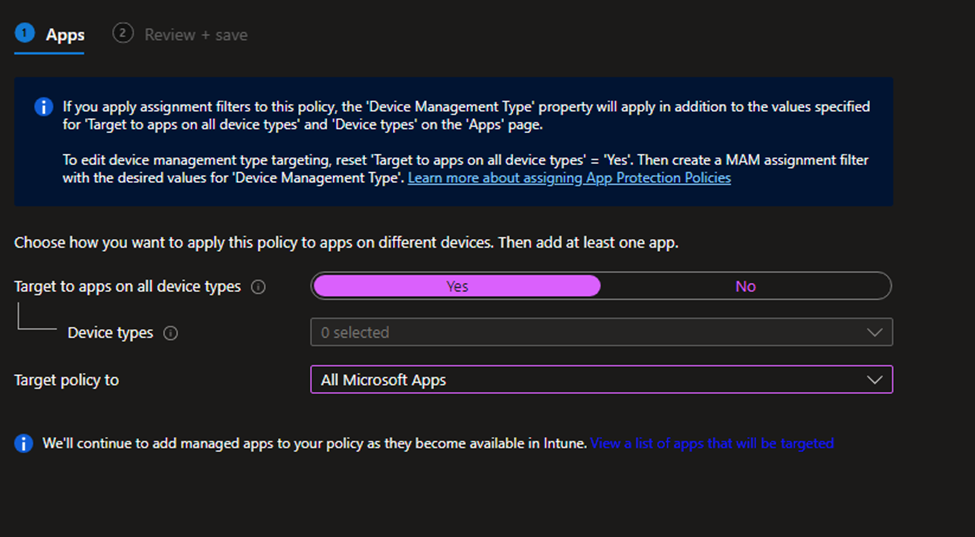
Apps: Target to apps on all device types Yes
Device types: Grayed out, this is for Manage or Unmanage devices.
Target policy to: you can select All Apps, All Microsoft Apps, Core Microsoft Apps, 3 different list of apps. I selected All Microsoft Apps.
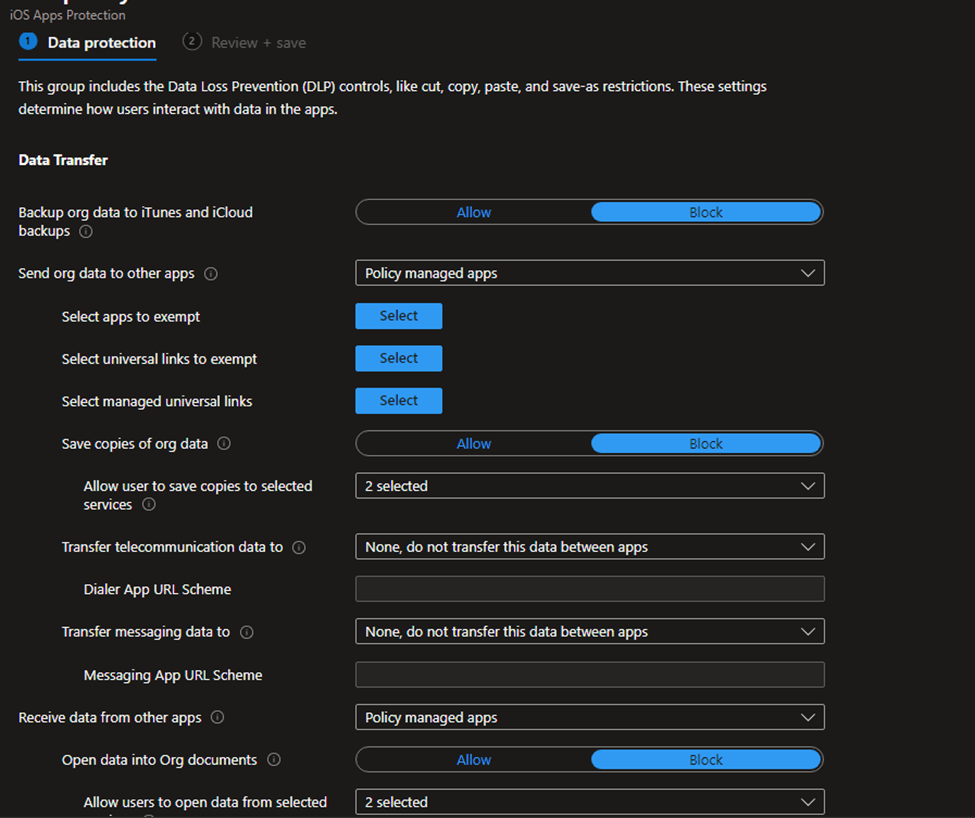
Data Protection: I will show many options below in my screenshots; I will only explain what is applicable to my project.
Backup org data to iTunes and iCloud backups: Blocked backup org’s data from back up to Apple iCloud or iTunes.
Send org data to other apps: you can allow All, None, or Selected Apps, I went with Policy Managed apps.
Saved copied of org data: Block.
Allow user to save copied to selected services: You deselect all, phone library, local storage, box, I select Org’ SharePoint and OneDrive for Business. In this case the user ONLY can save Org data in Org OneDrive for Business and SharePoint.
Transfer telecommunication data to: None.
Transfer messaging data to: None.
Receive data from other apps: You can select None, All, All Apps with ongoing org data, or Policy managed apps.
Open data into org doc.: Block
Allow user to open data from selected services: Photo library, camera, SharePoint, OneDrive for Business, I picked only OneDrive and SharePoint.
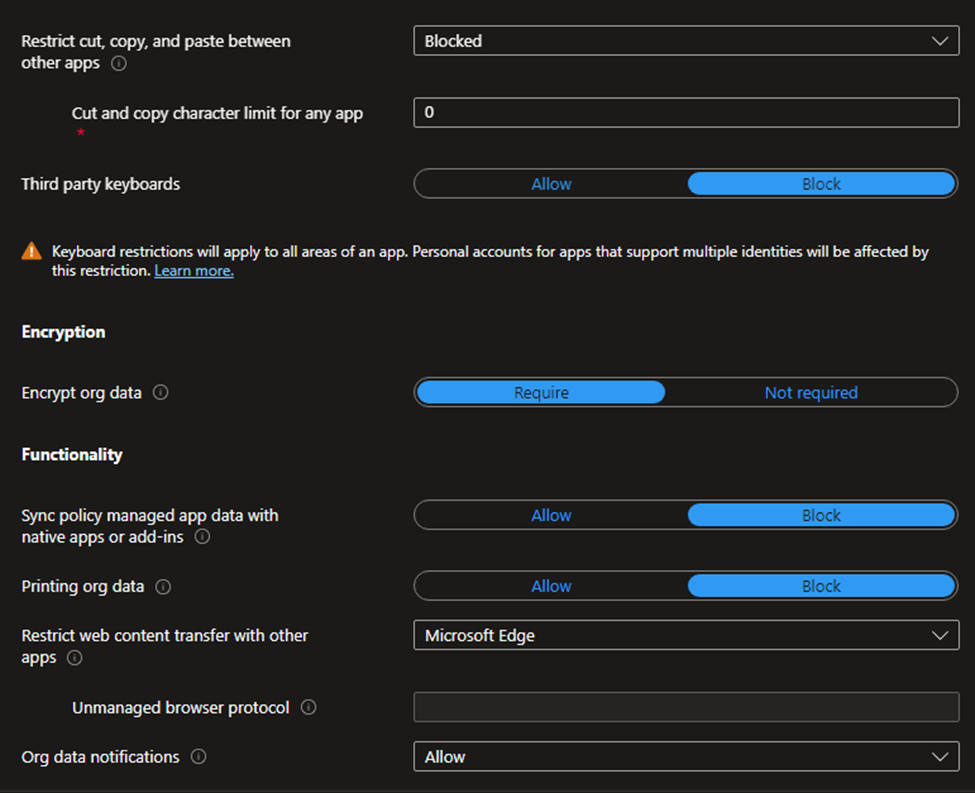
Restrict cut, copy, and paste between other apps: Block.
Cut and copy character limit for any app: you can allow between 0 (none) to 65535 letters.
Third party keyboards: Block.
Encryption org data: Require.
Sync policy managed app data..: Block
Print org data: Block.
Restrict web content transfer with other apps: Microsoft Edge.
Org data notification: Allow.
Access requirements:
PIN: Require. (to access to org apps you need a PIN for more security). You have multiple options here.
Timeout: between 30 – 65535 in Minutes.
FaceID instead of PIN for access iOS and iPadOS: Allow.
You can select a number of days to allow the user to rest the PIN: No.
App PIN when device PIN is set: Require.
Work or school account: Require.
Recheck the access: between 30 – 65535 in Minutes.
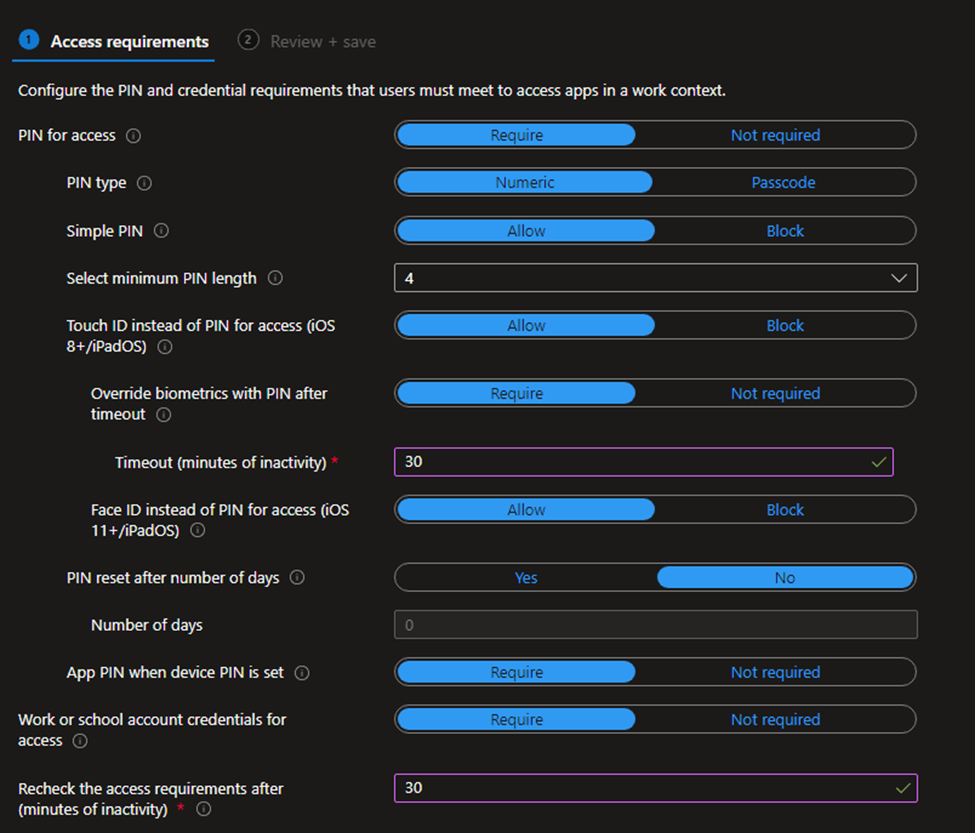
Conditional Launch: Default.
Assignments: assigned to a user or group of users.
Before I move to the next step, this setting above you can use it for Android as well, except Android has an amazing option not available in iOS: Screen Capture and Google Assistant: Block. If blocked, both screen capture and Google Assistant app scanning capabilities will be disabled when using the policy-managed app. This feature supports the usual Google Assistant app. Third party assistants using Google’s Assist API are not supported. Choosing Block will also blur the App-Switcher preview image when using the app with a work or school account.

4. Configure Access Control via SharePoint:
You may ask me why SharePoint, while the Cyber Security team was asking you about Teams, recently found out Teams data while saving in the cloud SharePoint.
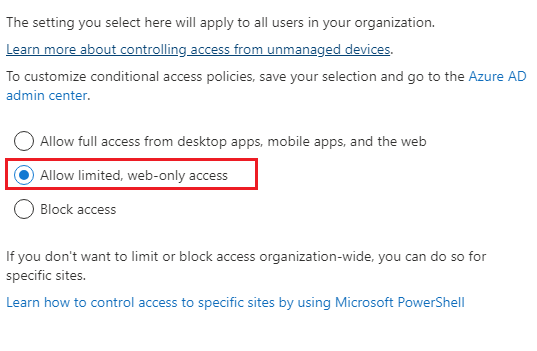
If you go to your SharePoint Admin Center> Policies> Access Control> you will see an option “Unmanaged Devices” to restrict access from devices that aren’t compliant or joined to the domain, once you click on it you will have 3 options
-Allow full access from desktop apps, mobile apps, and the web.
-Allow limited, wen-only access. ( I selected this option).
-Block access.

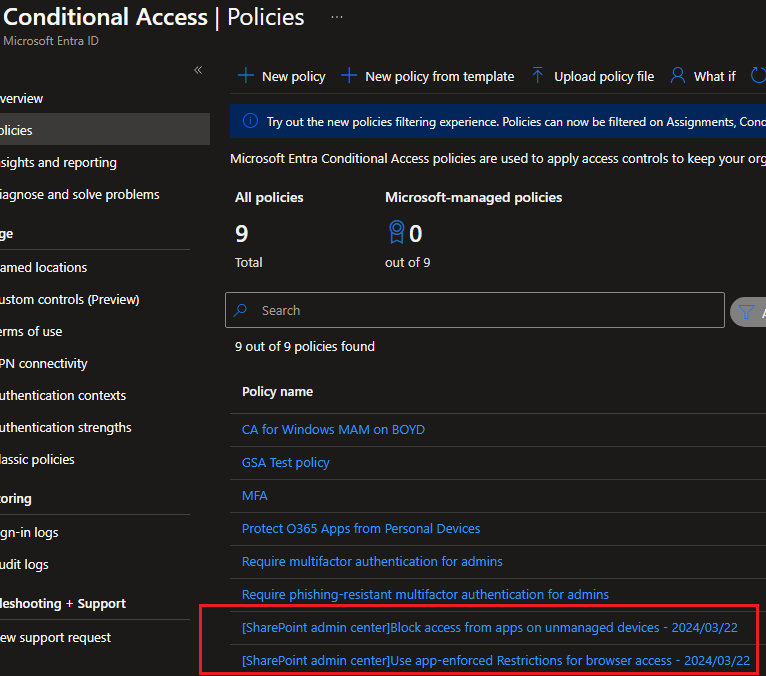
This Option will create 2 CAs, you have to go and check them and select what matches your Org security.
First, to block access from unmanaged devices. This is by Default.
In this one you need to ensure “Mobile apps and desktop clients” option is selected, check Conditions>Client apps>.
Second, use app-enforced restrictions for browser access on unmanaged devices. (this is what you need to manage and select extra options.
Like Apps already select Office 365 SharePoint.

Platforms: I selected iOS, Android, and Windows.
Client apps: Browser.
Session: Use app enforced restrictions.
Below are the screenshots from Windows, iPhone & Android Apps: