Since COVID-19, many users have started working from home until the same time, many end users like to use their personal devices to check their email over Outlook, Teams, SharePoint, and other M365 products, which is fine, but recently, many companies have been worried about their own Docs. To be copied, printed, downloaded, etc.
Here is what Conditional Access (CA) has to help us, since November 2023, during Microsoft Takeoff event when they released some new CAs, I started to test this, and just today, I finally was able to emblement this CA to do what has designed to do.
Setting up MAM for Windows
- Configure Condition Access.
- Configure App Protection Setting.
- Configure App Config Policies.
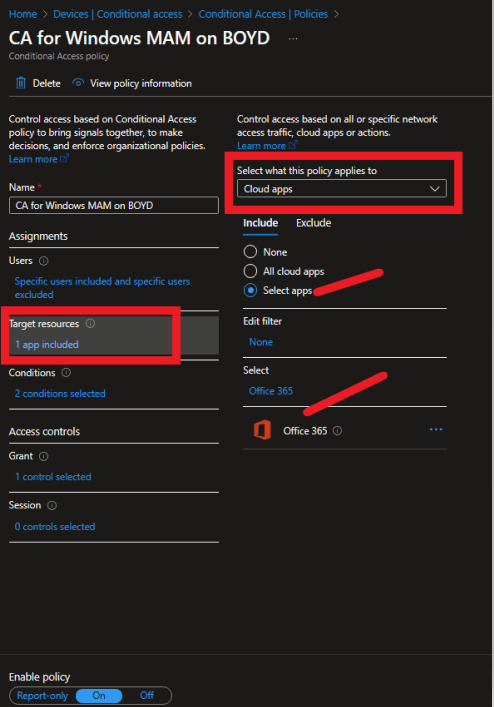
Configure Condition Access.
You can do that from Entra Admin Center or Intune Admin
Name: Name the CA .
Assignments: I selected all users, you can also target a group (good for testing)
Note: DO NOT forget to exclude your Global Admins or Roles to avoid locking yourself out. It happened to me one time before by mistake .
Target resources: you can select what you want to target, in this demo, I target cloud apps, specifically Office 365.
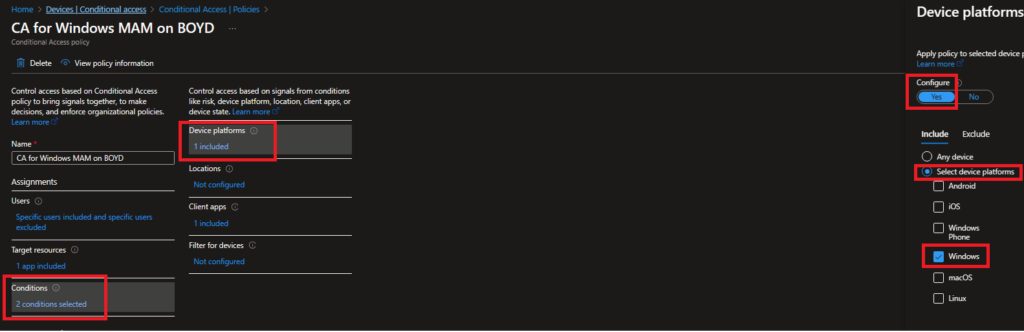
Conditions: I select Device Platform Windows.
Location: I did not configure.
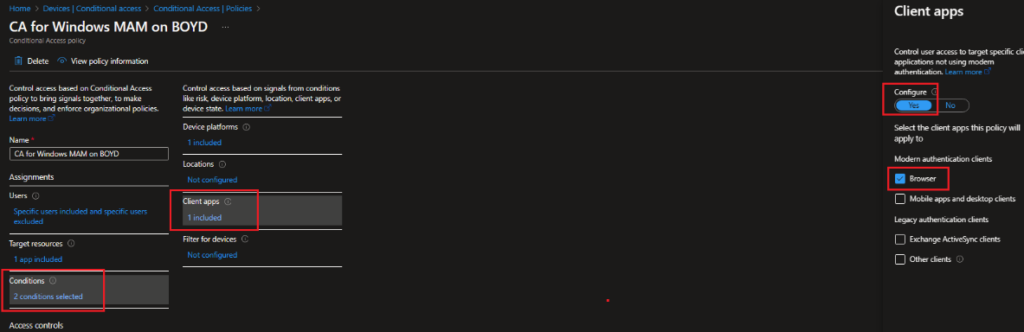
Client Apps: Browser.
Filter for devices: I did not configure.
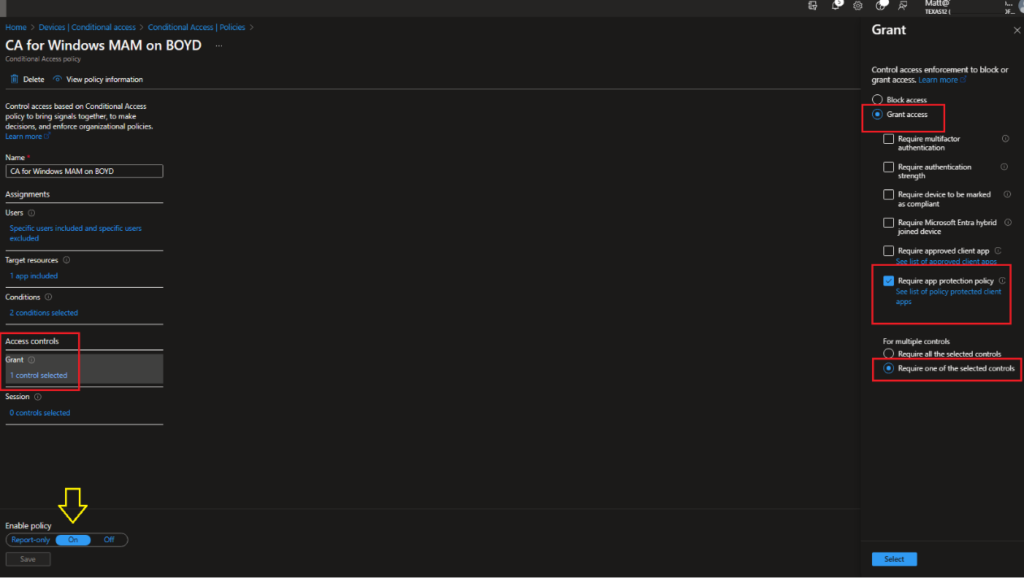
Grant: select Grant Access, then check “Require app protection policy”.
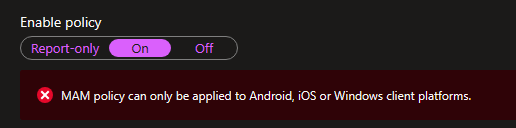
Note: you can change the enable policy to On now or place it on Report-only. Then, once you finish the other setting, you can go back and turn it on. And is this the first time you will get a notification with a link, and you have to click on it to enable it?
Configure App Protection Setting
Here we need to create a new App protection to protect our cloud app which is Microsoft Edge in this case,
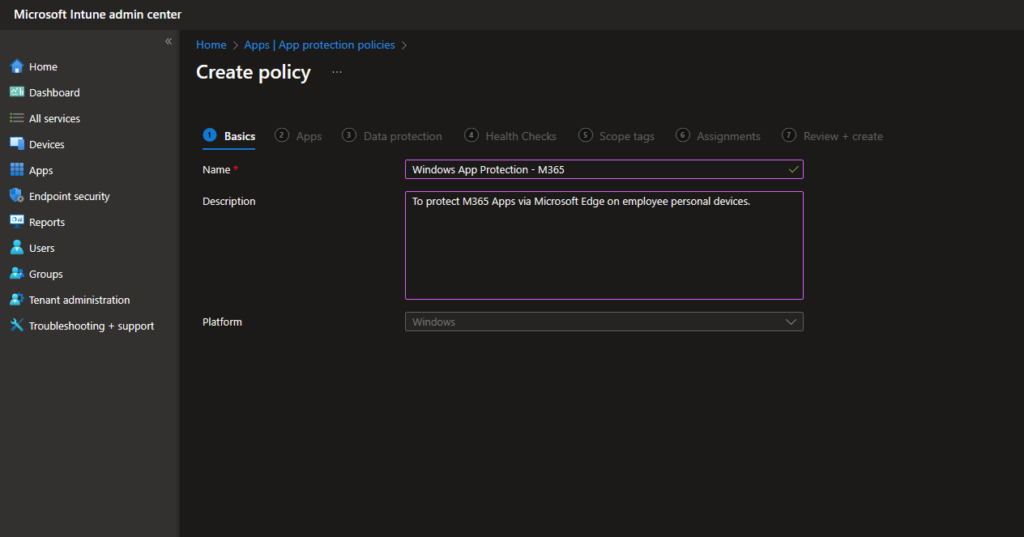
From Intune Admin center> Apps> App protection policies> create a new policy:
Basic
Name: Name it
Description: Optional
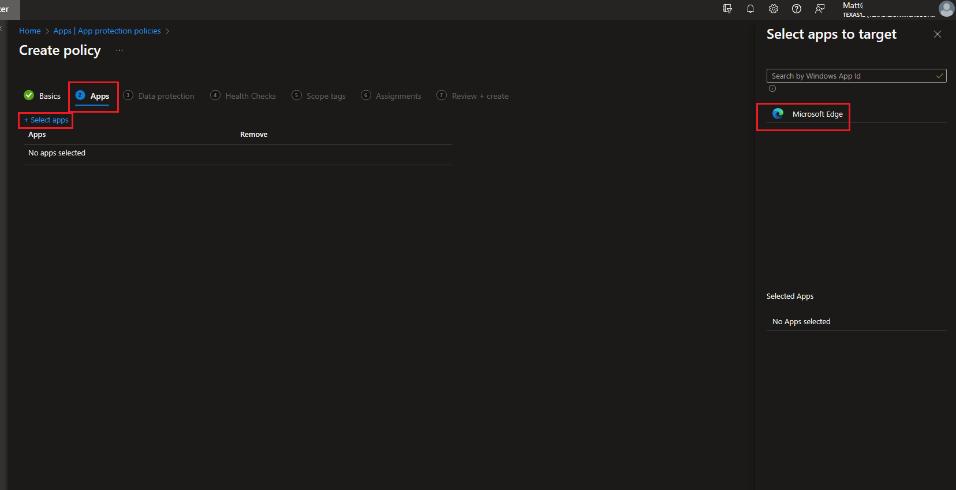
Apps
Select the Apps: you have one option, which is Microsoft Edge.
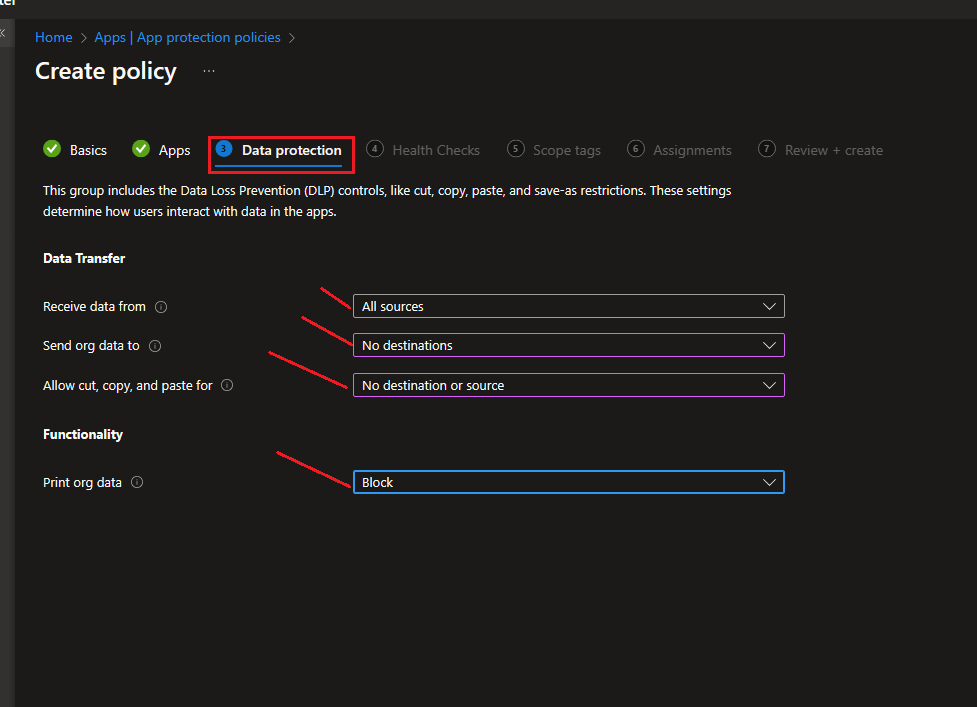
Data protection
Data transfer: here is what you need to configure whether your company will allow the end users to copy, paste, print, etc., or not.
In this demo, I blocked everything so the end-user could read only.
Receive data from: No source.
Send org data to: No destinations.
Allow cut, copy, and paste for: No destination or source.
Functionality
Print org data: Block
For Health Checks, you can determine what OS can log; in my case, I did not configure it.
Assignments: assign it to the group of user(s) I assigned to the same group I assigned the CA to.
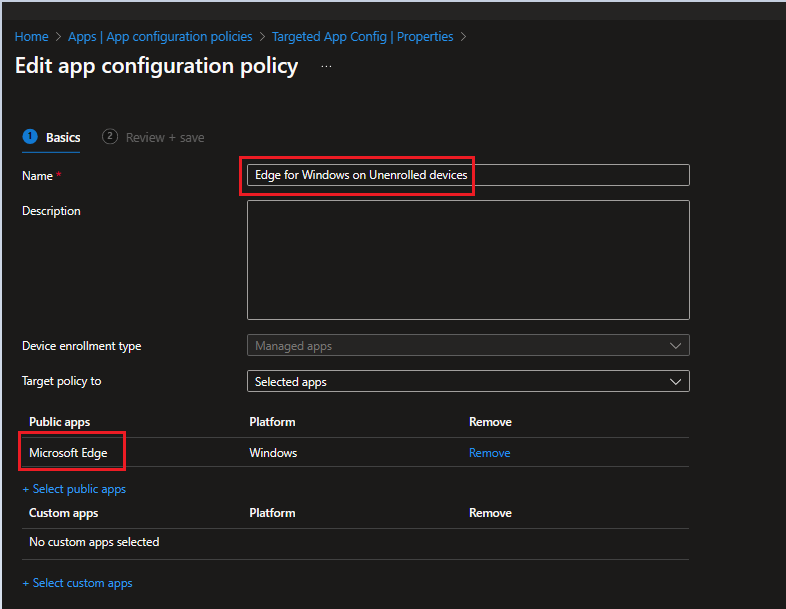
Configure App Config Policies
From Intune Admin center> click on Apps> App configuration policies click on Add, then select Manage Apps to create a new policy.
Name: Give it a Name.
Description: Optional.
Target Policy to: Select App “Microsoft Edge”
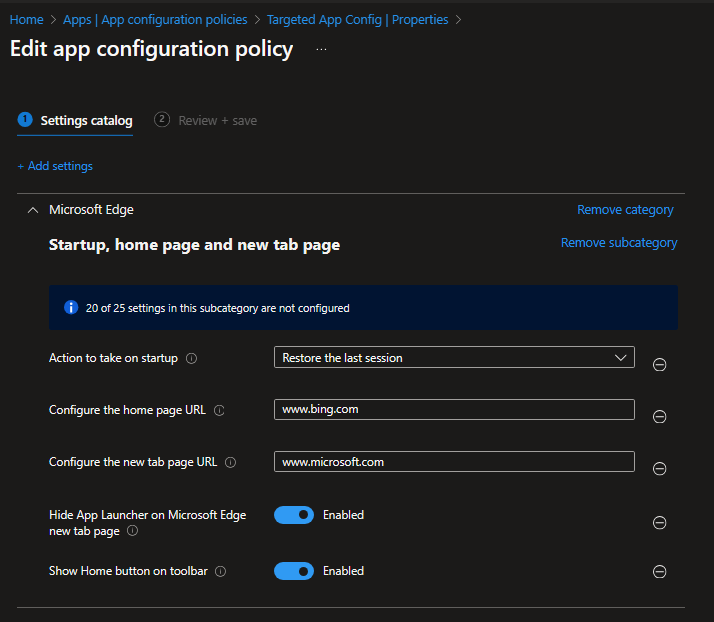
Setting Catalog
You can select whatever options you want. In my case, I selected the home page URL and new tab.
Assignments
I assigned it to the same users group.
Now let’s log in to the personal device and try to sign in to the office.com
First, I used different browsers like Google Chrome and Firefox to test it, and the CA re-directed me to Microsoft Edge.
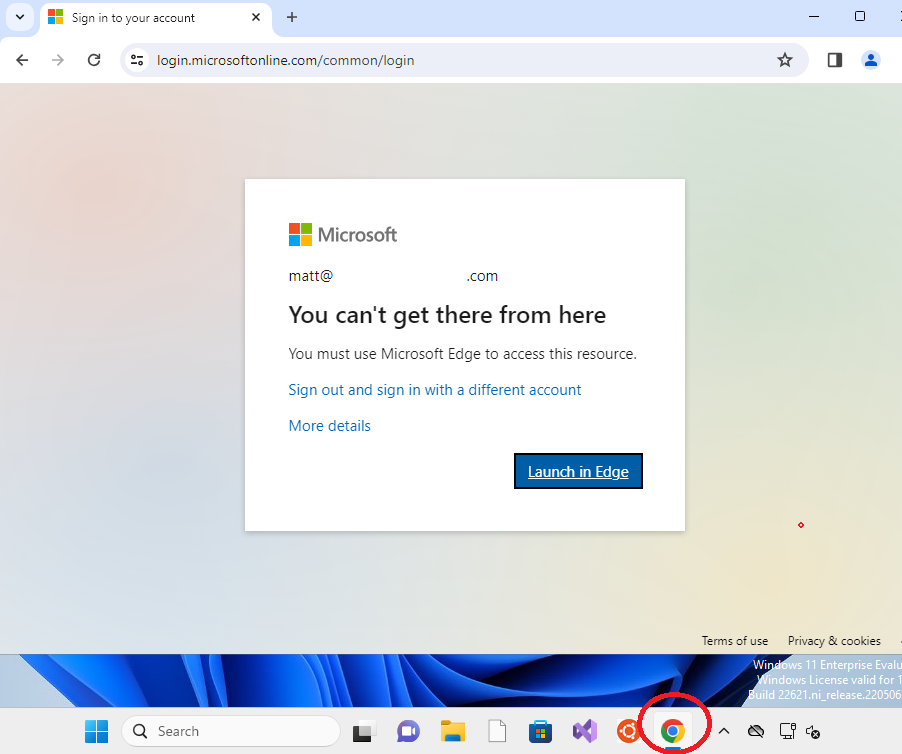
Click on “Launch in Edge”
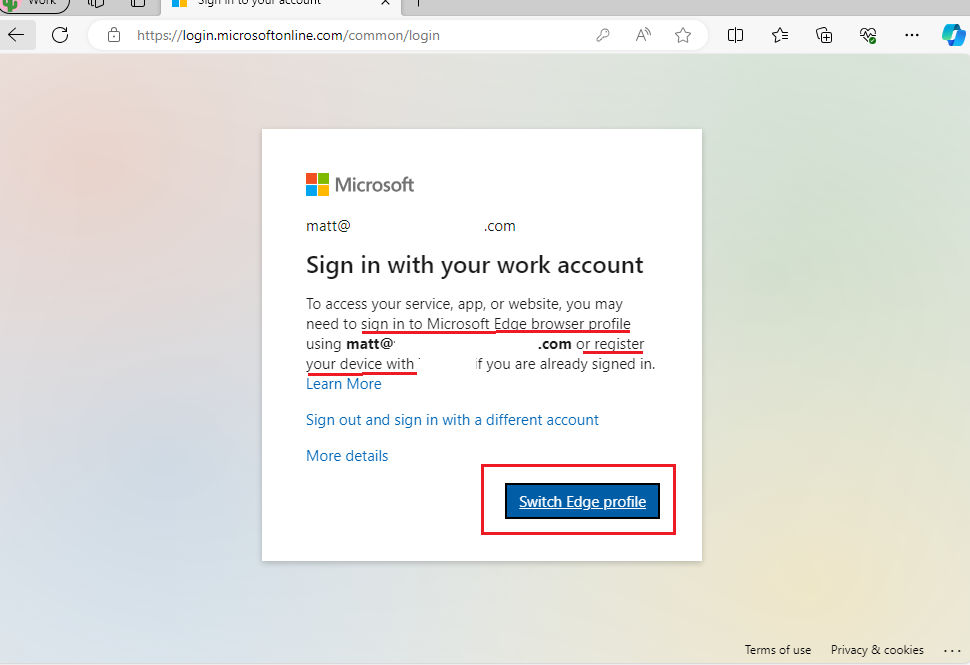
Here, the App Protection policy is enforcing the end user to use a switch from personal profile to Work profile, then you have to click on the profile from the top of the screen and ensure to uncheck the box so Intune cannot manage your device just this application.
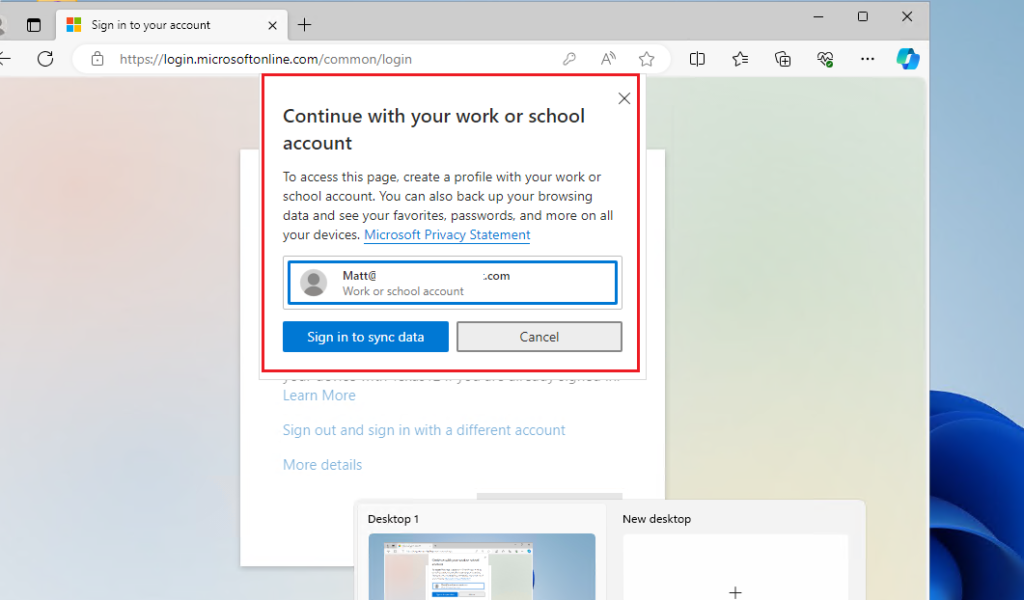
You must CLEAR THE CHECKBOX Allow my organization to manage my device. Leaving this checked enrolls your device in mobile device management (MDM) not mobile application management (MAM).
Don’t select No, sign in to this app only.
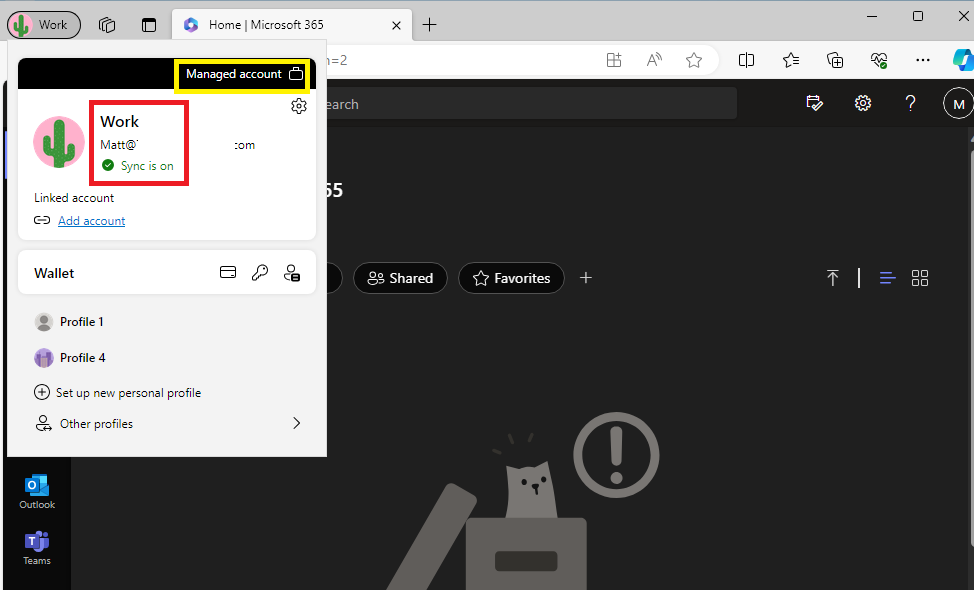
Below, you can see I logged on to the office with a Work account instead of my personal account.
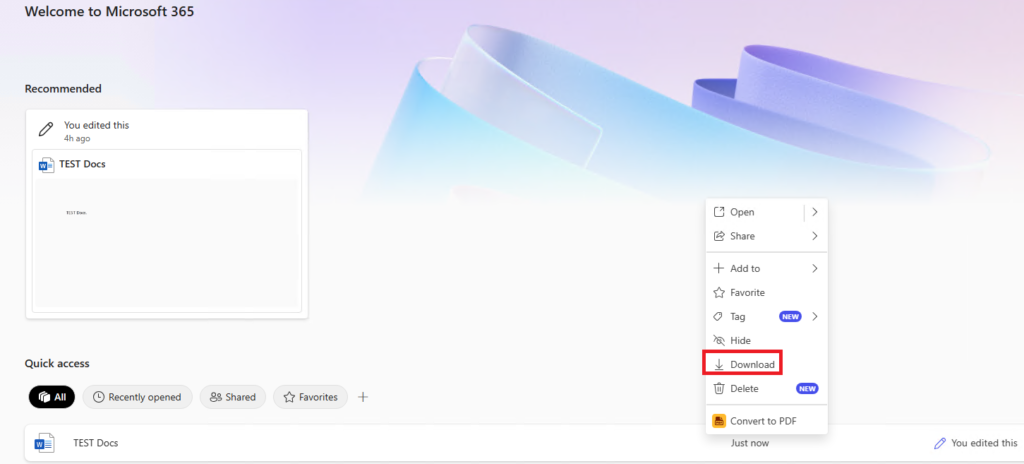
Let me open a file and try to test copy, print, download, etc.
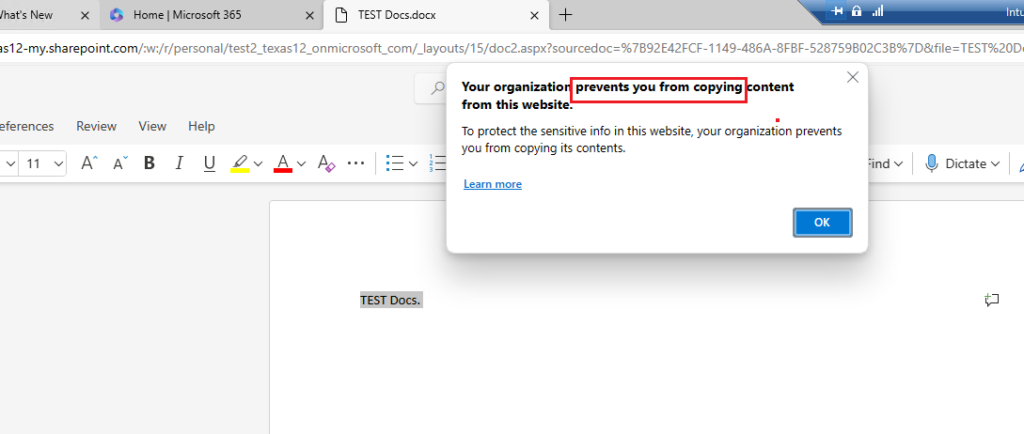
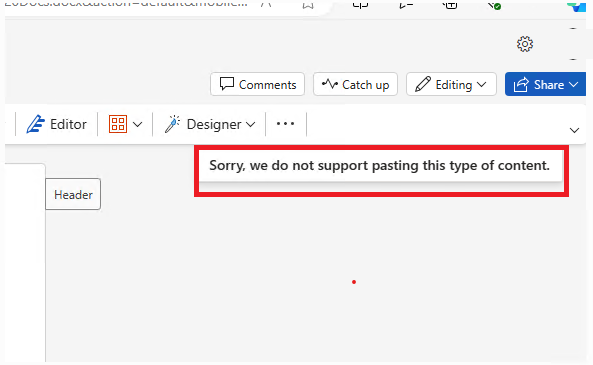
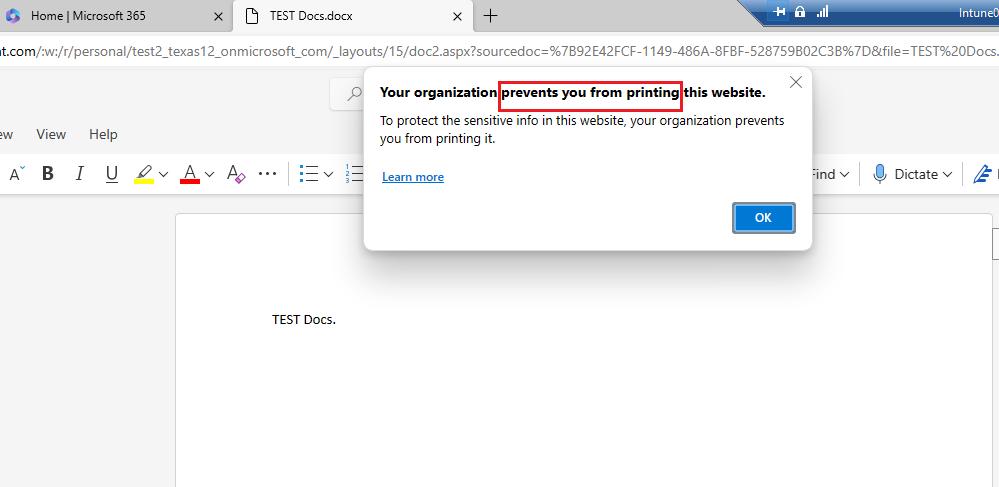
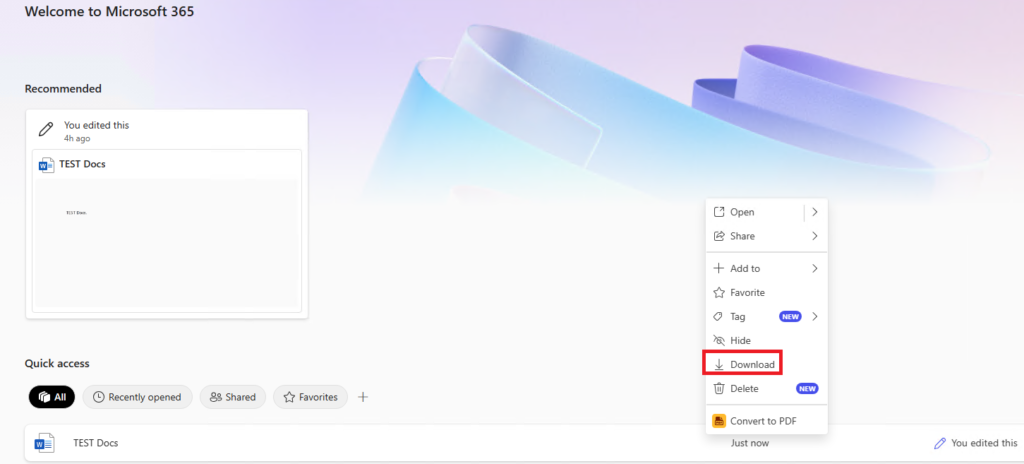
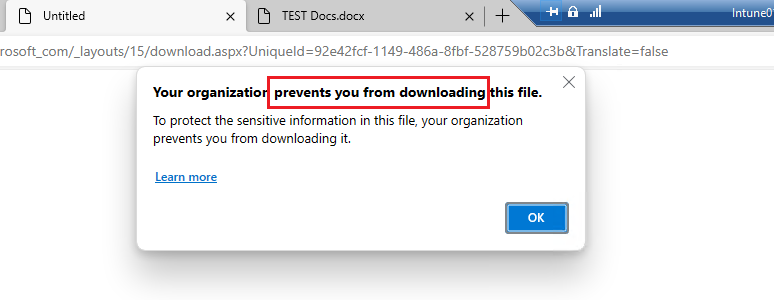
Great, so the CA, App protection, and App config policy are all working, let us finally look at the logs.
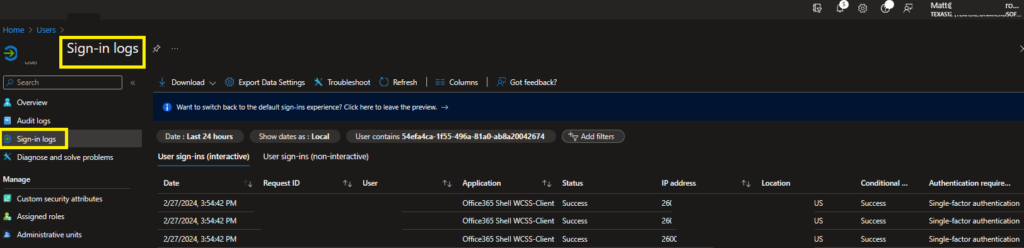
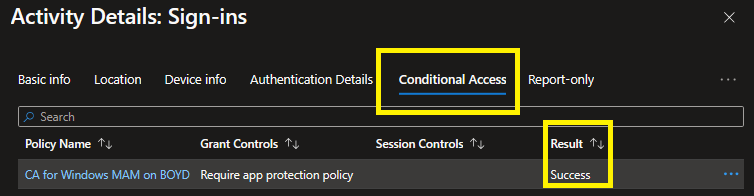
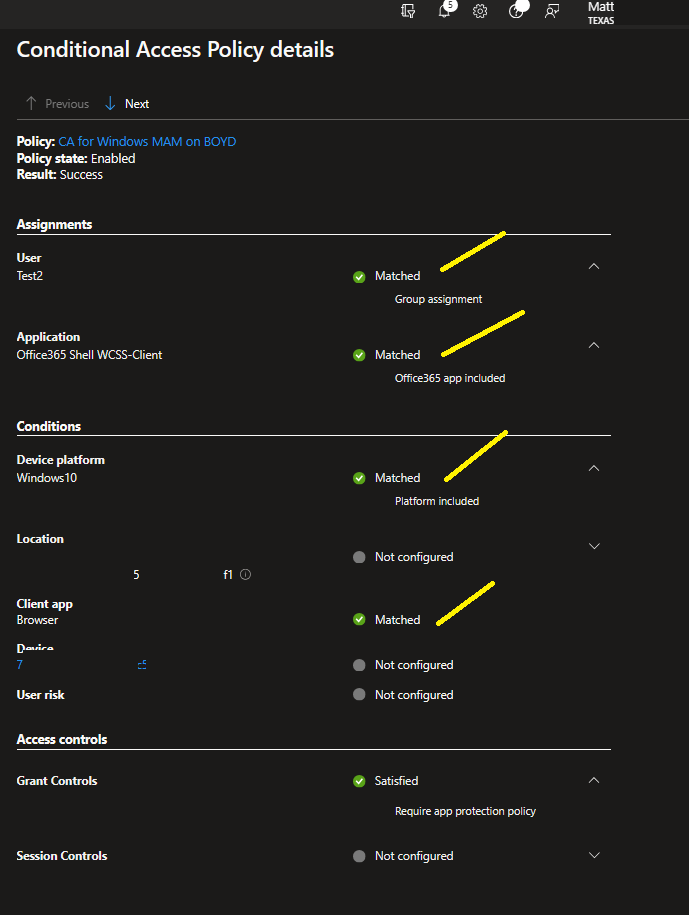
Conclusion
This conditional access is critical to implement it through your Org, which many companies have to block the end-user completely. So now you can let them log in with read permission Only if they prefer to use a personal device or in an emergency in which they do not have access to the corporate devices.
Important Note: You may force an issue when you click on Switch Profile on Edge, which keeps you in the same loop repeatedly. After long troubleshooting, which Microsoft did not mention anywhere, or I may have missed it, if the personal device has registered with another Org or school account, it will not apply this protect app policy until you remove them all.
Thanks for reading, I am hoping this may help y’all.
References:
Plan a Microsoft Entra Conditional Access deployment – Microsoft Entra ID | Microsoft Learn