Windows Appxpackage Vulnerabilitis
Hi Everyone,
Recently I saw many vulnerabilities with Windows AppxPackage. According to Tenable, these Apps need to get an update ASAP or remove.
Print 3D: the host may be affected by a remote code execution vulnerability, upgrade to the Microsoft 3D Builder app via the Windows App Store which is not available anymore.
VP9 Extension: the host may be affected by a remote code execution vulnerability, upgrade to app version 1.0.41182.0, or later via the Microsoft Store.
WebP Image Extension: the host may be affected by a remote code execution vulnerability, upgrade to app version 1.0.31251.0, or later via the Microsoft Store.
CVE: CVE-2020-1574
CVE: CVE-2021-31967
CVE: CVE-2023-23378
Below, this is what I found as a solution for each one,
Print3D, Unfortunately I do not see any update available for it, and even with Windows updates and I do not see it, so my recommendation is to remove
ensure you have it by running Get-AppxPackage -AllUsers | Where-Object {$_.Name -like "*Microsoft.Print3d*"}
if you found it just run the command with PachageFullName Remove-AppxPackage -Package "Microsoft.Print3D_3.3.791.0_x64__8wekyb3d8bbwe"
If you have more than one machine and want to remove the App from all of them you can create your script via SCCM and deploy it to all machines, or create CI/CB and let it work to discover and then remediate.
For VP9 and Web Image Apps, you can update them both from SCCM if you have it connected to Microsoft Store for Business, or from Inune which I use it here. I will use VP9 as an example and the process will be the same for WebP Image.
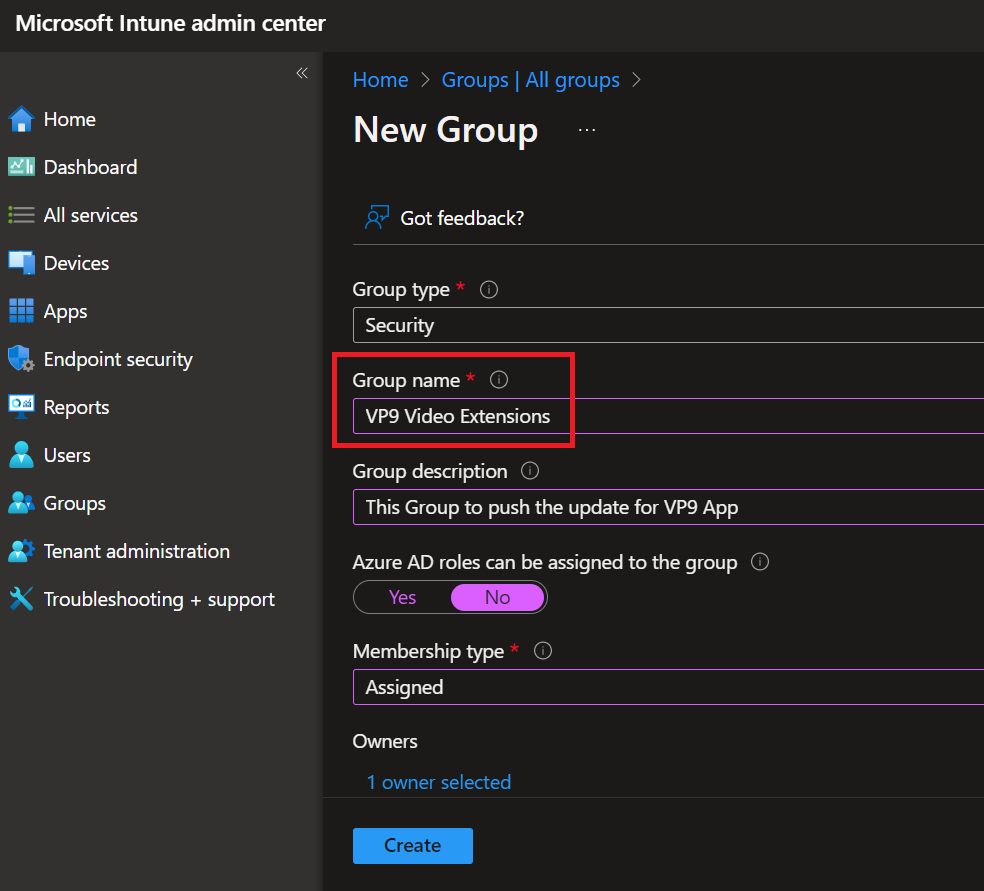
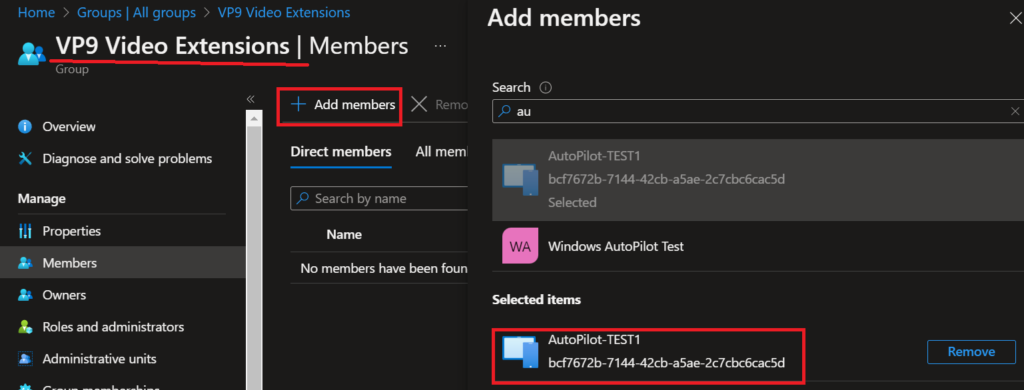
- I like to create a security group first and I will in Intune name it.
- Then let us find the app by adding App from All Apps:
- Select the source of the App from Microsoft Store App
- from Microsoft Store list search for VP9 app then select it.
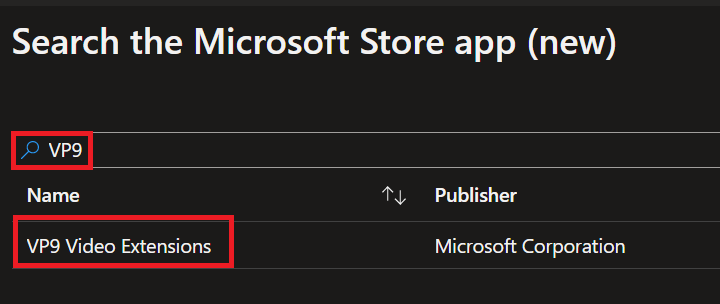
- Let us start configuring the app under App information
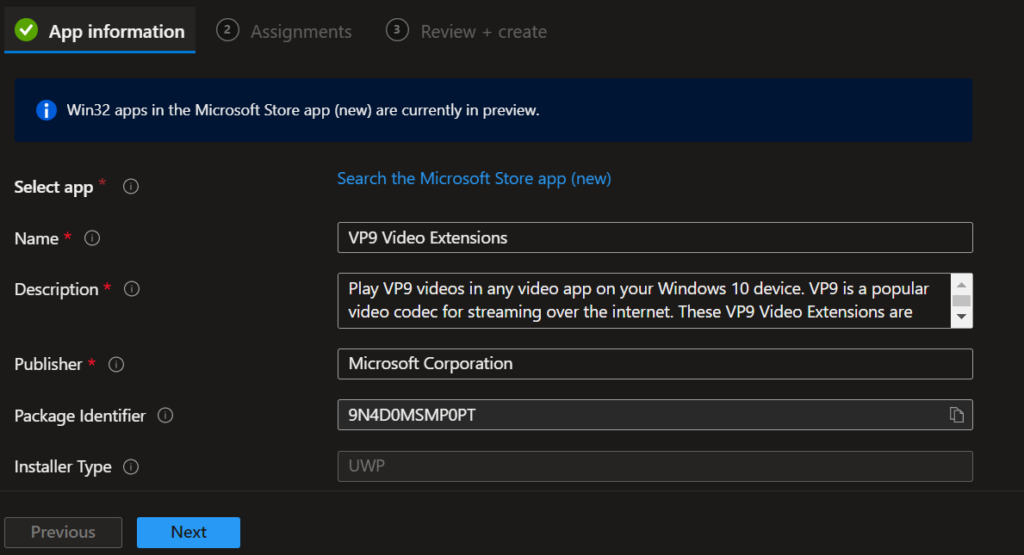
- Let us assign the app to a Group of Users, Devices, Group, etc. I will select the security Group I create in the first step above.

- Then review and finish the process, I did not add any device to the group, so I will add one device to it, in my test environment I add my “AutoPilot-Test1 machine
- because I deployed the app as Required not Available so the app will be installed, let us check my device
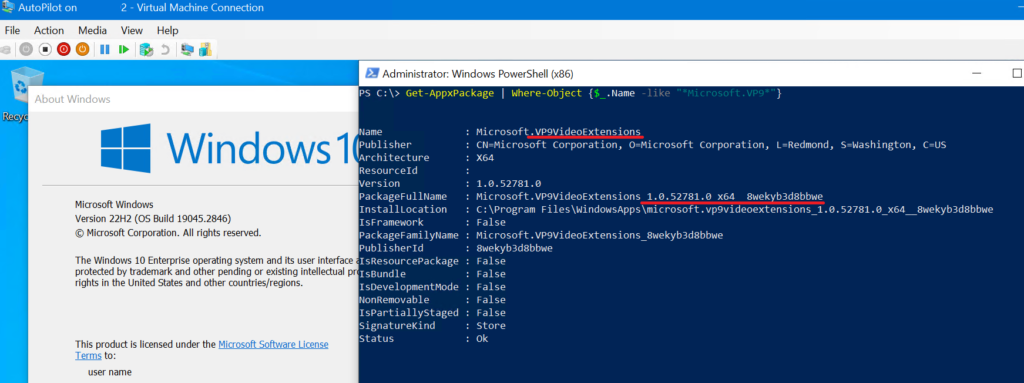

I hope this will help to fix the vulnerabilities.
Thanks for your time.